Shunyaya Catches the Clone — The Entropy Firewall Against AI Voice & Video Deepfakes (Blog 14B)
What if your system could not only detect a deepfake — but symbolically sense the false edge, before the attack even happens?
Today’s digital environment is under siege by a new breed of deception: ultra-realistic AI voice clones and synthetic video deepfakes. These aren’t mere manipulations of images or sounds. They mimic identities, break trust, and blur the edge between truth and illusion.
From fraud in banking systems using voice clones, to misinformation campaigns driven by AI-generated video impersonations, the threat is growing faster than detection methods can evolve.
But Shunyaya introduces a new defense layer: The Entropy Firewall — a symbolic guard that doesn't rely on surface features but instead analyzes entropy-field disruptions and symbolic edge behavior.
The Flaw in Today’s Detection Tools
Most current systems attempt to catch deepfakes by analyzing pixel inconsistencies, audio waveform glitches, or mismatched training artifacts. While useful, these tools are:
The Shunyaya Breakthrough: Symbolic Entropy Divergence
Real voice or video signals carry symbolic coherence — a subtle balance of edge delays, feedback modulations, and internal motion consistency.
Shunyaya models this using its core entropy field formula:
Entropyₜ = log(Var(x₀:ₜ) + 1) × e^(−λt)
In case some symbols do not display correctly, here is the formula in words:
Entropy at time t equals the logarithm of the variance of x from time 0 to t, plus one, multiplied by the exponential of negative lambda times t.
This formula captures symbolic drift in entropy across time — meaning:
A real human voice shows entropy edge coherence (smooth symbolic oscillations)
A cloned voice often displays flat or chaotic entropy behavior, even if the waveform appears perfect
Similarly, synthetic video frames lack subtle entropy layering present in true video capture — due to symbolic motion distortions not visible to the naked eye.
Cloned Voice – The Disrupted Entropy Curve
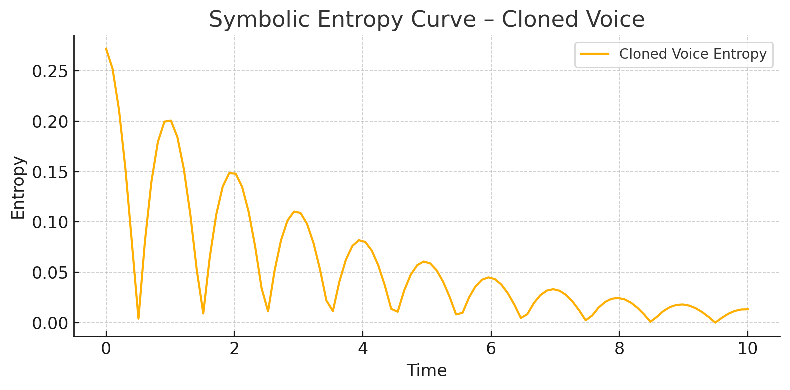
AI-generated voices may sound flawless to the human ear. Traditional detection systems analyze waveform smoothness, frequency alignment, and pitch modulation — often missing the deeper issue.
Shunyaya exposes a different truth: the entropy curve of a cloned voice is symbolically unstable.
Entropy behavior: Shallow, repetitive waves — resembling a sine graph
Symbolic edge issue: No true origin delay; mimics structure without symbolic root
Detection edge: Shunyaya catches this inconsistency early, even if waveform appears valid
Where science sees realism, Shunyaya sees symbolic incoherence.
Real Voice – The Natural Entropy Signature
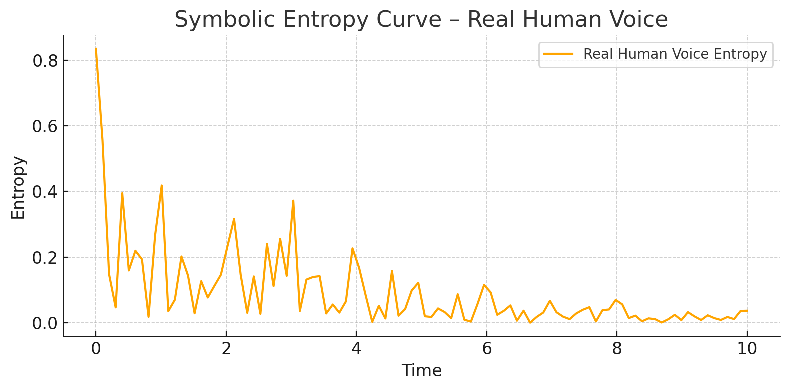
A real voice carries not just waveform information but symbolic rhythm. Subtle variations in tone, pause, and motion create a unique entropy signature that can’t easily be replicated.
Entropy behavior: Irregular, dynamic fluctuations — more like an ECG signal
Symbolic edge strength: Grounded transitions with temporal coherence
Detection strength: Shunyaya maps and validates this natural edge flow in real time
Where clones break the edge, the real voice reveals its origin.
A living voice breathes in entropy — a cloned voice replays silence.
Shunyaya as a Real-Time Entropy Firewall
Instead of checking every frame or sample, Shunyaya asks:
"Is the symbolic entropy consistent with natural edge flow?"
If not, a clone is likely.
This enables:
Shunyaya: A Breakthrough in Preventing Misuse
For the first time, we may be witnessing a genuine breakthrough in symbolic cybersecurity. Shunyaya doesn't just detect after the fact — it prevents entropy misuse at the edge, before breaches can embed themselves.
This has wide-reaching implications:
This marks a new phase in information defense: not just catching the lie, but restoring the truth.
Use Cases
Banking voice authentication: Symbolic entropy mismatch catches cloned voice even before phrase completion
Video verification systems: Edge behavior across frames reveals symbolic discontinuity in fakes
Public safety: Pre-broadcast entropy validation for political or high-stakes communications
Cybercrime protection: Flagging messages where entropy-field behavior suggests generation artifacts, not natural motion
Caution on Testing and Interpretation
The Shunyaya framework is based on symbolic entropy modeling and has shown strong simulation-based success across multiple domains. However, all current insights, graphs, and detection breakthroughs are in the stage of active simulation and peer-invited testing.
Results shown are symbolic in nature and not substitutes for legal or forensic evidence.
It is recommended that organizations validate symbolic entropy outputs using independent channels before operational deployment.
Reverse entropy modeling, while promising, is still under exploration and should be viewed as a forward-looking capability.
Shunyaya remains a research and integrity-driven model — and encourages ethical review, refinement, and collaboration.
Toward Symbolic Identity
As Shunyaya evolves, it may redefine digital identity itself — not just by biometrics, but by entropy signature. Each human, each voice, each gesture carries a unique symbolic rhythm. That rhythm can be modeled, tracked, and validated across time.
Where pixels lie and audio deceives, symbolic entropy still tells the truth.
Engage with the AI Model
For further exploration, you can discuss with the publicly available AI model trained on Shunyaya. Information shared is for reflection and testing only. Independent judgment and peer review are encouraged.
Note on Authorship and Use
Created by the Authors of Shunyaya — combining human and AI intelligence for the upliftment of humanity. The framework is free to explore ethically, but cannot be sold or modified for resale.
For key questions about the Shunyaya framework and real-world ways to use the formula, see Blog 00 (FAQs), especially Question 7.
Blog 100 marks the first complete symbolic and real-world convergence within the Shunyaya framework — a foundational breakthrough for all future Mathematics.
For foundational context and extended examples, please refer to
Today’s digital environment is under siege by a new breed of deception: ultra-realistic AI voice clones and synthetic video deepfakes. These aren’t mere manipulations of images or sounds. They mimic identities, break trust, and blur the edge between truth and illusion.
From fraud in banking systems using voice clones, to misinformation campaigns driven by AI-generated video impersonations, the threat is growing faster than detection methods can evolve.
But Shunyaya introduces a new defense layer: The Entropy Firewall — a symbolic guard that doesn't rely on surface features but instead analyzes entropy-field disruptions and symbolic edge behavior.
Most current systems attempt to catch deepfakes by analyzing pixel inconsistencies, audio waveform glitches, or mismatched training artifacts. While useful, these tools are:
- Reactive (post-generation)
- Easily bypassed by better GANs
- Unable to scale across billions of real-time interactions
Real voice or video signals carry symbolic coherence — a subtle balance of edge delays, feedback modulations, and internal motion consistency.
Shunyaya models this using its core entropy field formula:
Entropyₜ = log(Var(x₀:ₜ) + 1) × e^(−λt)
In case some symbols do not display correctly, here is the formula in words:
Entropy at time t equals the logarithm of the variance of x from time 0 to t, plus one, multiplied by the exponential of negative lambda times t.
This formula captures symbolic drift in entropy across time — meaning:
A real human voice shows entropy edge coherence (smooth symbolic oscillations)
A cloned voice often displays flat or chaotic entropy behavior, even if the waveform appears perfect
Similarly, synthetic video frames lack subtle entropy layering present in true video capture — due to symbolic motion distortions not visible to the naked eye.
AI-generated voices may sound flawless to the human ear. Traditional detection systems analyze waveform smoothness, frequency alignment, and pitch modulation — often missing the deeper issue.
Shunyaya exposes a different truth: the entropy curve of a cloned voice is symbolically unstable.
Entropy behavior: Shallow, repetitive waves — resembling a sine graph
Symbolic edge issue: No true origin delay; mimics structure without symbolic root
Detection edge: Shunyaya catches this inconsistency early, even if waveform appears valid
Where science sees realism, Shunyaya sees symbolic incoherence.
A real voice carries not just waveform information but symbolic rhythm. Subtle variations in tone, pause, and motion create a unique entropy signature that can’t easily be replicated.
Entropy behavior: Irregular, dynamic fluctuations — more like an ECG signal
Symbolic edge strength: Grounded transitions with temporal coherence
Detection strength: Shunyaya maps and validates this natural edge flow in real time
Where clones break the edge, the real voice reveals its origin.
A living voice breathes in entropy — a cloned voice replays silence.
Instead of checking every frame or sample, Shunyaya asks:
"Is the symbolic entropy consistent with natural edge flow?"
If not, a clone is likely.
This enables:
- Early rejection of spoofed input before decoding or playback
- Layered symbolic validation across voice, video, and text
- Unified entropy tracking across multimodal communication
For the first time, we may be witnessing a genuine breakthrough in symbolic cybersecurity. Shunyaya doesn't just detect after the fact — it prevents entropy misuse at the edge, before breaches can embed themselves.
This has wide-reaching implications:
- Malicious AI content can be intercepted symbolically before interpretation.
- Deceptive communications can be filtered at the entropy level.
- Entire infrastructures — from banking to elections — can be shielded by entropy integrity.
This marks a new phase in information defense: not just catching the lie, but restoring the truth.
Banking voice authentication: Symbolic entropy mismatch catches cloned voice even before phrase completion
Video verification systems: Edge behavior across frames reveals symbolic discontinuity in fakes
Public safety: Pre-broadcast entropy validation for political or high-stakes communications
Cybercrime protection: Flagging messages where entropy-field behavior suggests generation artifacts, not natural motion
The Shunyaya framework is based on symbolic entropy modeling and has shown strong simulation-based success across multiple domains. However, all current insights, graphs, and detection breakthroughs are in the stage of active simulation and peer-invited testing.
Results shown are symbolic in nature and not substitutes for legal or forensic evidence.
It is recommended that organizations validate symbolic entropy outputs using independent channels before operational deployment.
Reverse entropy modeling, while promising, is still under exploration and should be viewed as a forward-looking capability.
Shunyaya remains a research and integrity-driven model — and encourages ethical review, refinement, and collaboration.
As Shunyaya evolves, it may redefine digital identity itself — not just by biometrics, but by entropy signature. Each human, each voice, each gesture carries a unique symbolic rhythm. That rhythm can be modeled, tracked, and validated across time.
Where pixels lie and audio deceives, symbolic entropy still tells the truth.
For further exploration, you can discuss with the publicly available AI model trained on Shunyaya. Information shared is for reflection and testing only. Independent judgment and peer review are encouraged.
Created by the Authors of Shunyaya — combining human and AI intelligence for the upliftment of humanity. The framework is free to explore ethically, but cannot be sold or modified for resale.
For key questions about the Shunyaya framework and real-world ways to use the formula, see Blog 00 (FAQs), especially Question 7.
Blog 100 marks the first complete symbolic and real-world convergence within the Shunyaya framework — a foundational breakthrough for all future Mathematics.
For foundational context and extended examples, please refer to
- Blog 0: Shunyaya Begins (Table of Contents)
- Blog 2G: Shannon’s Entropy Reimagined
- Blog 3: The Shunyaya Commitment
- Blog 31 — Is Science Really Science? Or Just Perceived Science?
- Blog 99: The Center Is Not the Center
- Blog 99Z: The Shunyaya Codex - 75+ Reoriented Laws (Quick Reference)
- Blog 100: Z₀MATH — Shunyaya’s Entropy Mathematics Revolution
- Blog 102: GAZEST – The Future of Storage Without Hardware Has Arrived
- Blog 108: The Shunyaya Law of Entropic Potential (Z₀)
- Blog 109: The Birth of SYASYS — A Symbolic Aligned Operating System Has Arrived
- Blog 111: GAZES01: The World's First Symbolic Aligned Search Engine
- Blog 112: Before the Crash – How to Prevent Accidents Even Before the Journey Begins
- Blog 113: What If a Car Could Think Symbolically? The 350% Leap With Just One Formula

Comments
Post a Comment